What compliance is, and what it is NOT
 Friday, February 19, 2010 at 07:26AM
Friday, February 19, 2010 at 07:26AM A lot of what gets me in the door to discuss identity and access management is compliance. There are a lot of regulations out there for every country, individual regions of different countries, and of course all the verticals (banking and finance, healthcare, insurance, credit card, arms trade, telecomm, anybody who’s publicly traded, etc.). If you’re a publicly-traded US company, you have Sarbanes-Oxley. Even if you’re not in healthcare, you’ve got HIPAA (if you’re large enough). If you handle credit cards, you’ve got PCI. Most companies are subject to multiple compliance laws.
A lot of these laws share provisions, such as strong authentication, access control, attestation, protection of private data, and so on. If you know what those common elements are and institute them in your infrastructure, you can reasonably tell your auditors that you’re compliant, possibly with multiple provisions at a time. And here’s the thing that most C-level execs know: the definition of compliance is negotiable. Most of these laws are written so vaguely, they’re almost always subject to interpretation. PCI is part detail, part fog. SOX has spawned numerous lawsuits as a result. “What do you mean, I’m not compliant? In your face!”
Compliance is an essay question. “I am compliant, and I say this because I have policy-driven user enablement, I enforce segregation of duties, I encrypt private data, I regularly review access rights and make corrections as necessary, and I log all user and administrative actions.”
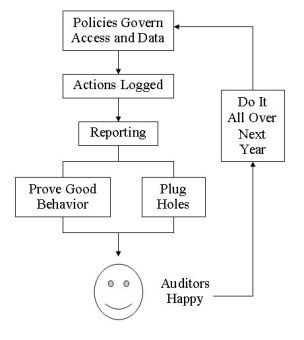
Therefore, with a proper identity and access framework in place, you might have to tweak things once in a while to make auditors happy, but in general you will pass most smell tests. Compliance equals the policies that you have in place to ensure least-privilege (everybody only gets access to what they should have, and nothing more). These policies grant privileges only to those who are eligible, and periodically checks to make sure that’s all they still have, because, y’know, stuff happens. So if you’re running an identity/access framework (eg. Oracle IAM suite), you’re enabling people at the door according to policy, governing their changes (promotion, demotion, transfer) according to policy, and using those same policies to decide how they leave at termination time. Here’s the stuff you can access, here’s the stuff you keep as you move through the organization over time, here’s the stuff you lose instantly when we catch you doing naughty stuff.
So here’s what compliance is NOT. It is not REPORTING. I hear that term all the time, “compliance reporting.” I hear “SOX reporting” more than I hear “SOX compliance.” It implies that if you can tell who did what and who has what, after the fact, then you’re compliant. Bzzzzt. Wrong. Reporting verifies that you have been compliant all along (or that you’ve been screwing up), but by itself, it doesn’t equal compliance.
Some laws, like Sarbanes-Oxley, are based on reporting. In fact, SOX is based on reporting two different ways. It’s largely enforced by reporting, and it governs reporting.
http://en.wikipedia.org/wiki/Sarbanes-Oxley_Act
Meanwhile, the Payment Card Industry standard naturally includes, but isn’t entirely dependent on, reporting, since what it’s really governing is data security.
http://security.arizona.edu/pci
This is not to say that reporting is worthless. Au contraire. Without evidence, you might as well have been sitting on your can while the vultures have been circling your data. You must prove that you are compliant. Anybody who’s ever sat through a security audit knows how ugly it can be for your entire staff. But if you can provide the reports you’ve been generating on a regular basis, along with any custom reports that are requested, and those reports prove that you’ve been enforcing proper policies on access control and privacy, you have put yourself in a good place.
And of course, reporting also tells you where those tweaks have to be made. The closer you get to full compliance and security, the less work you’ll have to do the following year, when the auditors show up again. And remember, compliance is only getting tougher, and new technology will require new efforts on your part. So doing it right now will make it easier to institute additional safeguards later. It also makes it easier to refine your policies and procedures each year after the auditors find something wrong, and they will, because that’s their job. Auditors do not get paid to tell you that you’re a genius. If there’s nothing wrong with your security and governance, guess what, there will be anway.
By the time I was through with high school, I wanted to skip graduation. Just give me the paper, and I’m done. But my dad explained it this way: if we didn’t go to the ceremony, with the cap and gown and “Pomp and Circumstance,” it was like I’d skipped high school altogether. And then mom would have made him kill me. So even though I had the education in my head, I needed the paper in a frame.
So both pieces are necessary, and while the paper by itself doesn’t make you any more secure, it shows the world what they need to know about you. So make yourself safe and compliant, and prepare to provide the evidence.
Reader Comments